Is Your SOC Audit Ready?
What happens when the auditor asks for documentation?
The Old Way

With Cydarm CIRM
Regulators don't just want to know what happened. They want a complete timeline: when you knew, what you did, and every decision in between. Pulling that together manually takes hours. Sometimes days.
Cydarm builds that timeline automatically as your team works the incident. Every action, every update, every decision, captured in real time.
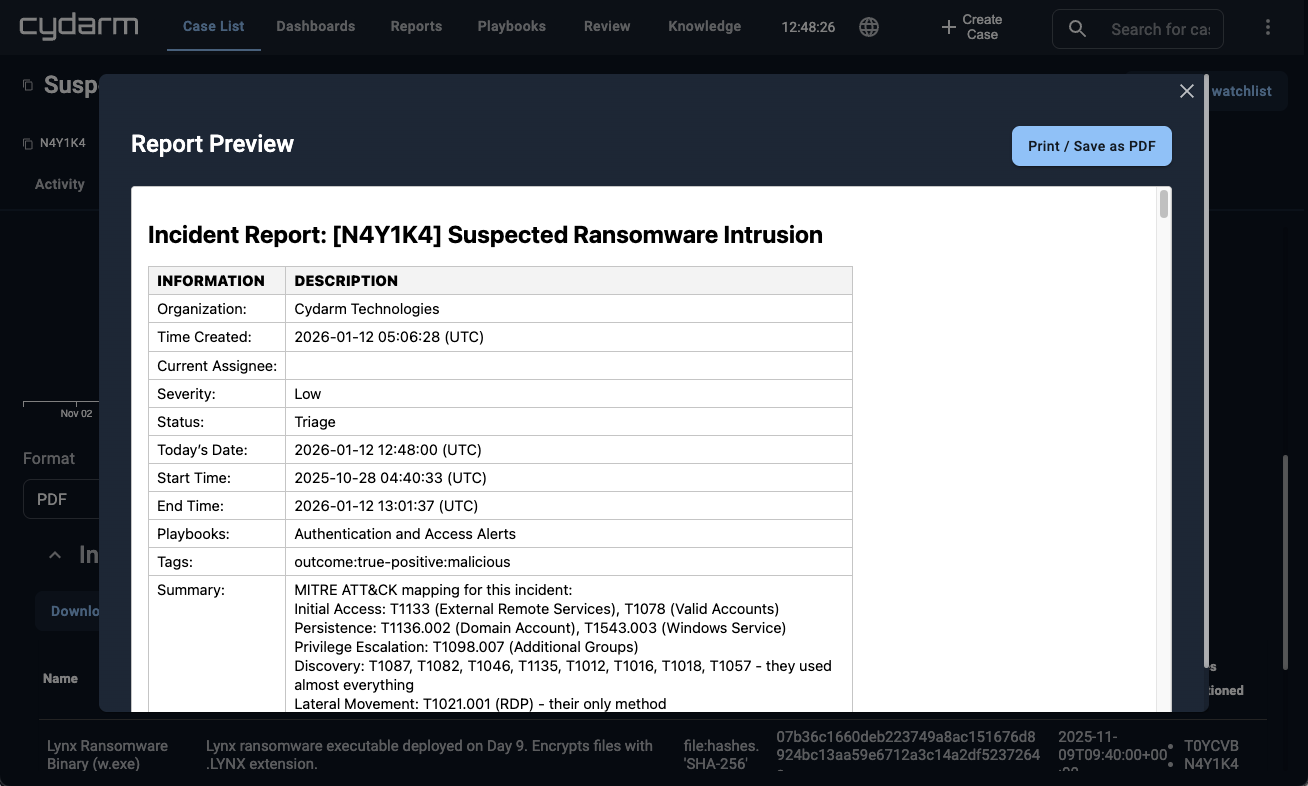
When the deadline hits, generate a complete audit-ready report in under 60 seconds.
Start Your Free Trial
What happens when the auditor asks for documentation?


* Hype CycleTM for Security Operations 2025, Cybersecurity Incident Response Management market category
You're not preparing for future regulations. You're already subject to them.
When an incident hits, you won't have time to figure out which deadlines apply. A single breach affecting customers in multiple states could trigger 10+ different notification requirements, each with different timelines, different notification thresholds, and different definitions of "personal information".
The question isn't whether you'll face regulatory scrutiny. It's whether you can prove what you did, when you did it, and why.
Contact Us To Find Out More:
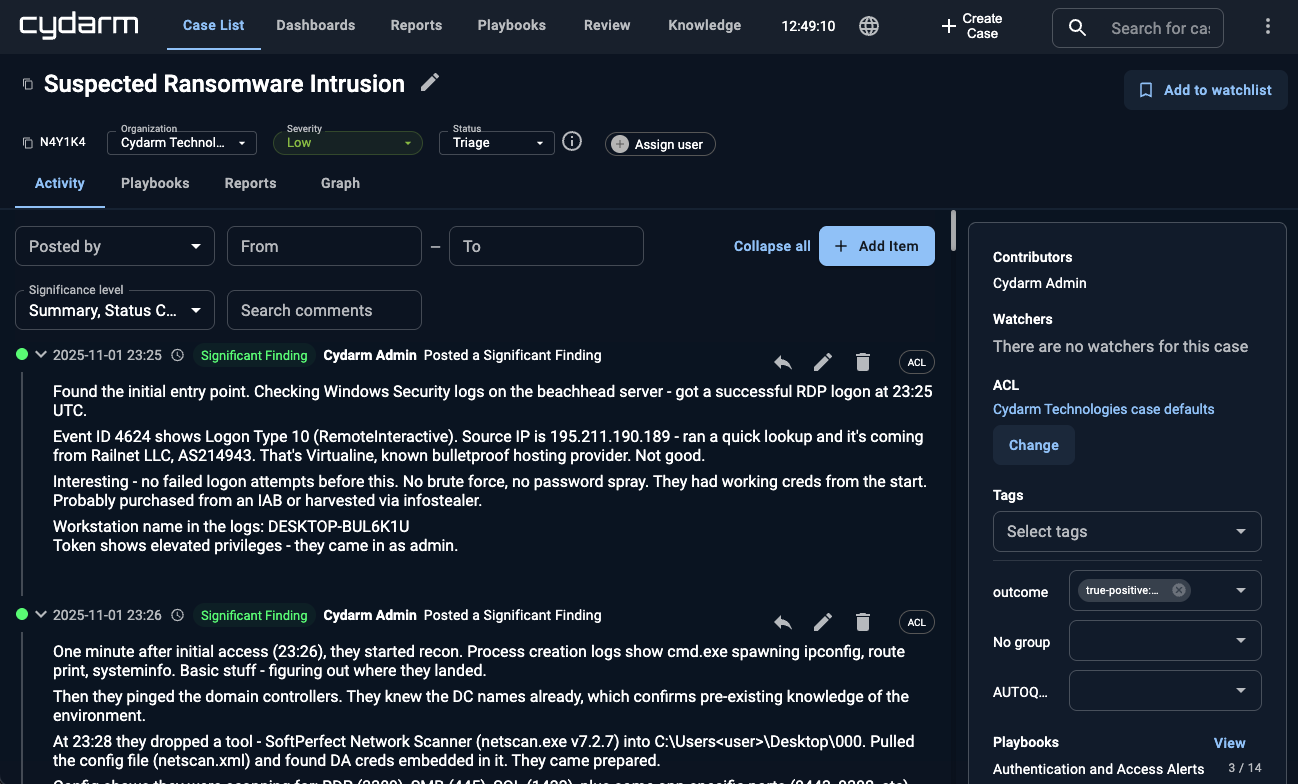
Most teams reconstruct incident timelines after the fact: digging through Slack, email, and tickets. Cydarm captures the timeline as you work.
And when someone remembers something later? Backdated notes let you add context pinned to when it actually happened - not when you remembered to write it down.

Cydarm isn't just for regulatory reporting. It's a complete Cyber Incident Response Management platform that handles the full lifecycle, from the moment an alert fires to the final post-incident review.
Whether you're a water utility triaging a suspicious OT alert, a bank coordinating a major fraud investigation, a defense contractor managing a nation-state intrusion, or a hospital responding to ransomware across 15 stakeholders, Cydarm keeps everyone aligned and everything documented.
Legal, communications, the CIO and other executives, regulators, and sometimes law enforcement all need updates, and they all need different information. Cydarm gives each stakeholder a role-appropriate view without duplicating effort or losing context.
Contact Us To Find Out More:
Some Incidents Require Need-to-Know Access
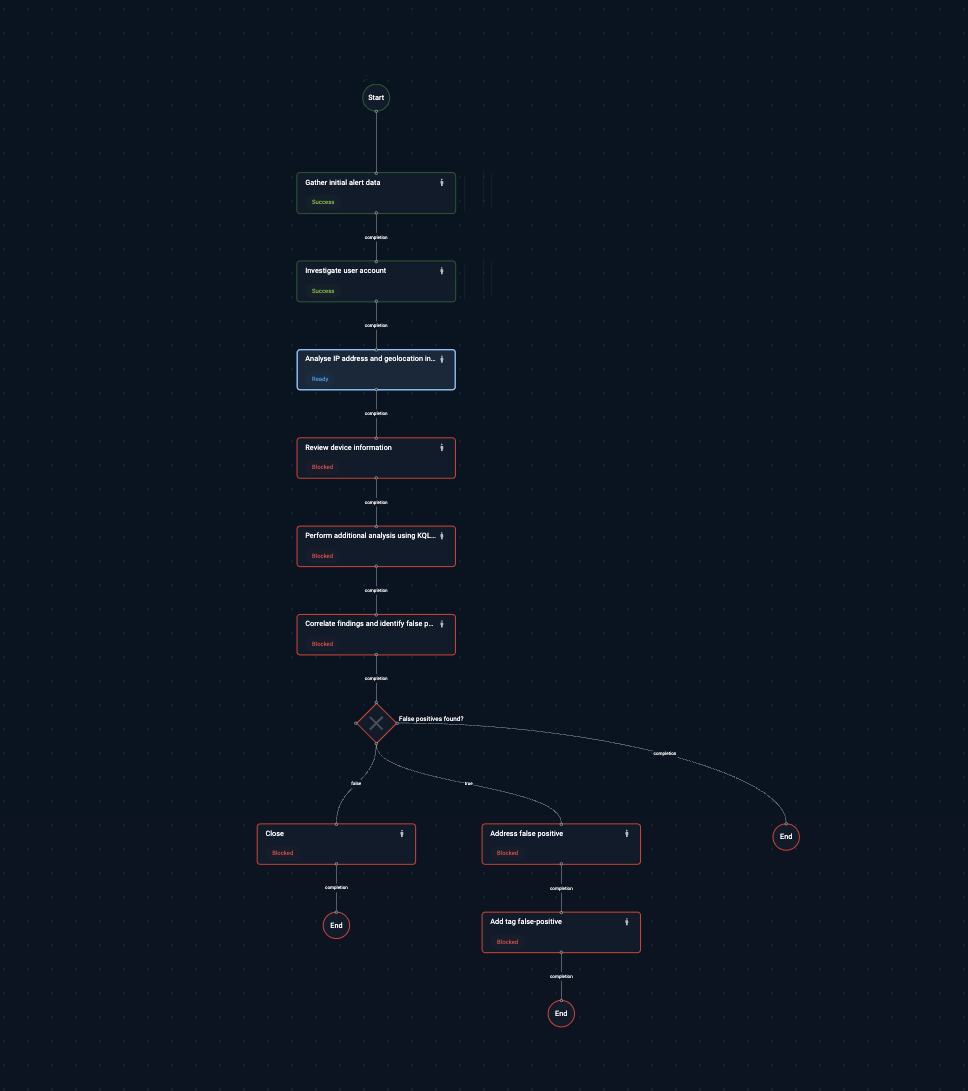
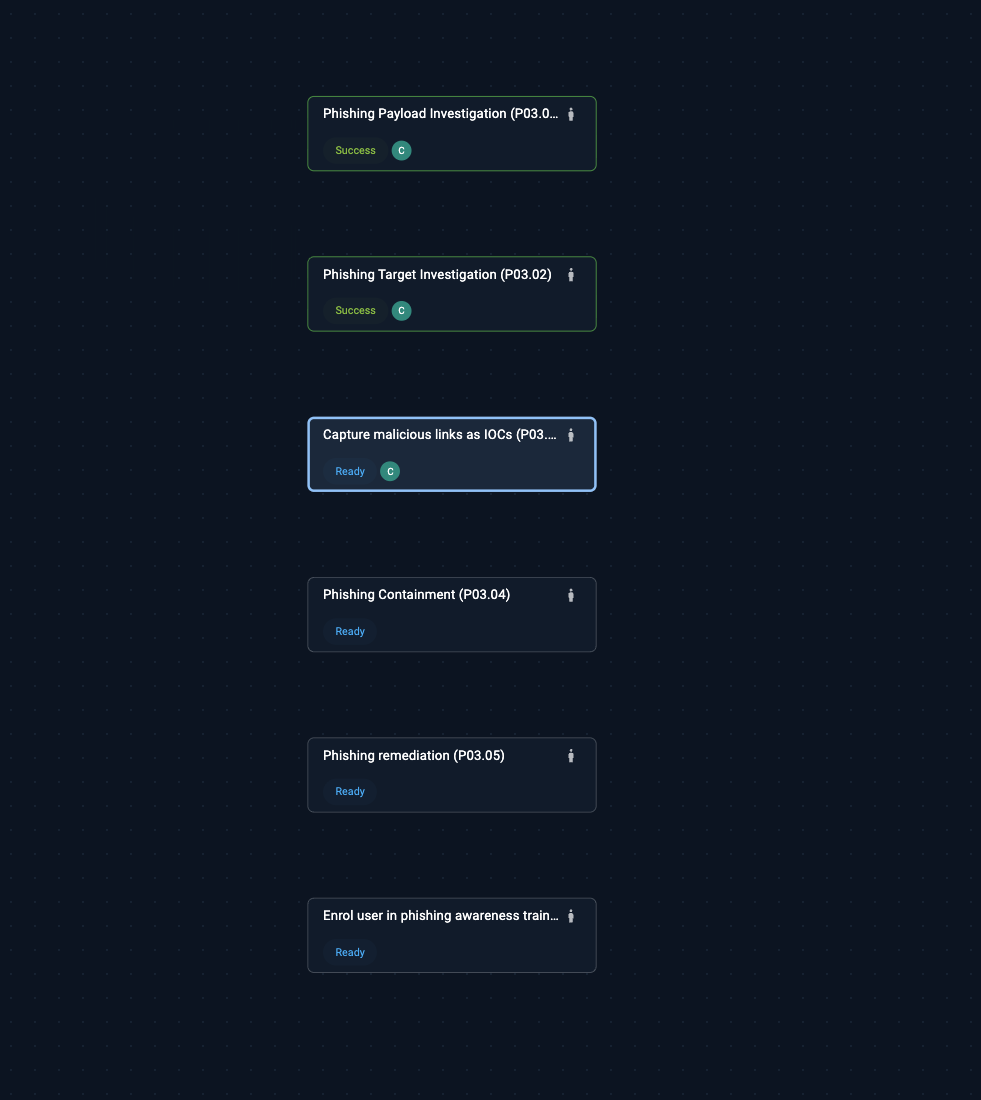
Not every investigation should be visible to your entire security team. Insider threat cases at a power utility. HR-related incidents at a defense contractor. Matters involving executives. Investigations where the suspect might have SOC access.Auditors don't just ask what you did - they ask whether you followed your own procedures. Cydarm's Playbooks and Checklists give you both:
• A standardized process your team can follow
• Notes against each step
• A record showing which steps were assigned and completed, when, and by whom
When someone skips a step or deviates from the playbook, that's captured too, along with the reason. No more "we usually do X" without evidence.
The next time a regulator asks what happened, will you have answers in under a minute - or spend 4 hours doing archaeology?
Start your free 30-day trial. No credit card required. No scripting needed. No implementation project. Just incident response documentation that works.
Start Your Free Trial
Or Contact Us To Find Out More: