After more than a decade, NIST has updated its incident response guidance, and the changes tell a story about how much the field has evolved. NIST SP 800-61r3 reflects what many practitioners have observed: incident response has become less about perfect procedures and more about building organizational cyber resilience.
What's Different This Time
The most noticeable change is philosophical. Where the previous version treated incident response as a distinct process with clear phases, the new guidance integrates it throughout an organization's broader cybersecurity risk management. This shift acknowledges something that became apparent over the past few years: incidents don't wait for convenient timing, and recovery often overlaps with ongoing response efforts.
The traditional circular model has been replaced with the six NIST Cybersecurity Framework (CSF) 2.0 functions, recognizing that preparation is not something you do between incidents - it's continuous.
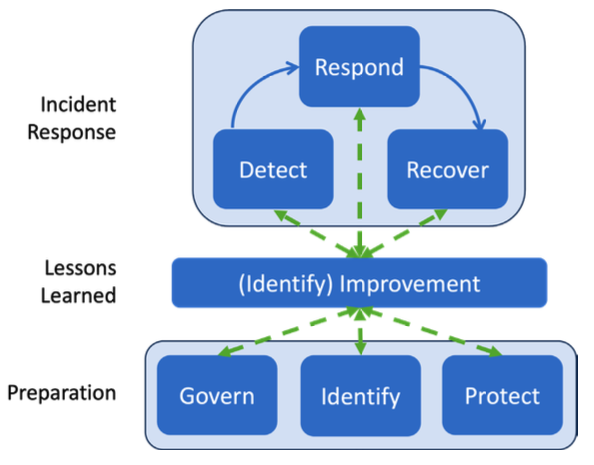
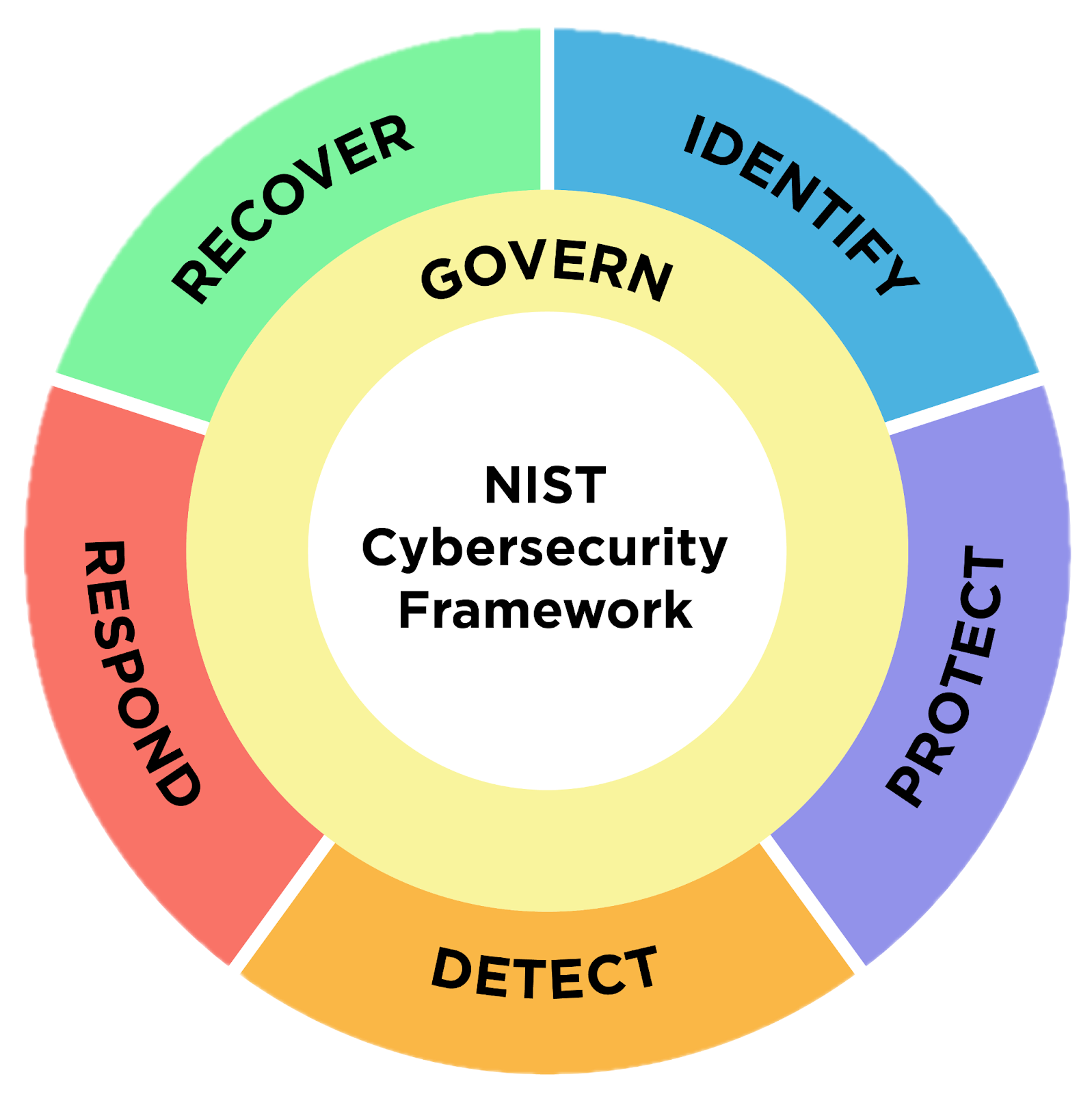
Practical Observations
Starting with Threat Intelligence
The guidance elevates cyber threat intelligence to "High" priority, which aligns with what incident responders have found useful. Organizations that regularly consume threat feeds tend to spot problems earlier. The practical challenge is not whether to use CTI, but finding feeds that provide actionable information without overwhelming your team.
The Reality of Continuous Monitoring
The emphasis on monitoring across all asset types reflects the expanded attack surface most organizations now face: networks, computing resources, physical environments, personnel activity, and third-party services. The guidance suggests automation where possible, which makes sense given the volume of events most teams encounter.
Moving Beyond First-Come, First-Served
The recommendation to prioritize incidents based on risk factors rather than arrival time addresses a common problem. Many organizations default to handling incidents in the order they're discovered, but this approach often misallocates limited response resources. Developing clear criteria takes time upfront but tends to improve outcomes when things get busy.
Accounting for Third Parties
Modern incidents often involve multiple organizations. The guidance acknowledges this reality with recommendations for clear communication channels, predefined authority levels, and information sharing agreements. These preparations can make the difference between coordinated response and confusion when service providers, cloud platforms, or internet service providers need to take action.
Ten Practical Steps Worth Considering
- Establish threat intelligence sources that match your environment and threat landscape. CTI functions as the early warning system across the entire incident lifecycle, feeding into risk assessments during the Identify phase, improving detection accuracy in monitoring systems, and providing crucial context during incident analysis and response. Organizations that integrate automated threat feeds into their SIEM platforms and SOC Case Management workflows can spot campaigns earlier and understand attacker methods more quickly, turning what might be reactive response into more informed, proactive defense.
- Deploy monitoring that covers all asset types, with automation where feasible. The goal is not perfect visibility but practical coverage that can identify anomalies and indicators of compromise before they become full incidents.
- Develop risk-based prioritization criteria before you need them. When multiple incidents occur simultaneously, clear prioritization criteria prevent teams from defaulting to first-come, first-served handling. These criteria should weigh factors like asset criticality, functional impact, data sensitivity, threat actor sophistication, and recovery complexity. Having these frameworks established during calm periods allows incident managers to make consistent decisions under pressure and allocate limited response resources where they'll have the most impact.
- Create communication channels with internal stakeholders and key third parties. Modern incidents cross functional boundaries within organizations and often extend beyond the organization. Complex incidents require coordination first with internal teams (e.g. legal, human resources, risk, executive leadership, and asset owners), as well as external partners such as cloud providers, internet service providers, managed security services, and supply chain vendors. Establishing internal and external escalation paths and communication protocols during preparation means you can activate coordinated responses quickly when incidents occur. A security Case Management system can define and automate much of this coordination. This includes defining decision-making hierarchies within the organization, clarifying authority levels for automated responses, and understanding what actions internal and external parties can take independently versus what requires explicit approval from management or legal teams.
- Build playbooks for your most common incident types. Effective playbooks translate general cybersecurity incident response procedures into specific, actionable steps for scenarios like ransomware infections, cloud service compromises, or supply chain incidents. These aren't rigid scripts but structured guides that help responders navigate complex situations consistently while allowing for situational adaptation. Well-designed playbooks also serve as training tools and help maintain institutional knowledge as team members change.
- Schedule regular exercises that include internal teams and critical partners. Exercises reveal gaps in procedures, communication channels, and coordination mechanisms that aren't apparent during normal operations. Tabletop discussions and simulations help teams practice decision-making under pressure and identify dependencies they hadn't considered. The inclusion of internal and external partners in these exercises strengthens the broader response ecosystem and clarifies roles.
- Verify backup integrity regularly and test restoration procedures. With ransomware and data destruction attacks becoming more sophisticated, backups serve as a critical recovery capability that must be protected and validated. This means not just ensuring backups are created, but confirming integrity is preserved, conducting restoration drills regularly (e.g. quarterly), and maintaining offline backup systems, isolated from production networks.
- Define recovery initiation criteria clearly. The transition from response to recovery is not always obvious, and starting recovery activities too early can interfere with ongoing containment efforts while waiting too long prolongs operational disruption. Clear criteria help incident managers balance the need for thorough investigation against business continuity requirements. These decisions often involve multiple stakeholders and benefit from predetermined frameworks that consider operational impact, evidence preservation needs, and resource availability.
- Establish continuous improvement mechanisms for ongoing refinement. The traditional model of conducting lessons learned sessions only after incident closure misses opportunities for real-time improvement. Effective organizations build mechanisms to capture insights during incidents: what's working, what is not, and what resources are needed. Using a Cybersecurity Case Management platform is an effective way to record information that leads to these insights. These insights are fed back back into procedures, training, and preparation activities immediately. This continuous refinement helps organizations adapt to evolving threats and operational changes.
- Plan communication strategies for different audiences and scenarios. Incident communication spans multiple domains: coordination among response teams, notification to affected parties, regulatory reporting, public communication, and executive reporting. Each audience has different information needs and timing requirements. Having communication frameworks established means teams can focus on content rather than figuring out processes during high-stress situations, and reduces the risk of inconsistent messaging or missed notifications.
The People Side
Perhaps the most practical insight in the updated guidance is the explicit recognition that cybersecurity incident response involves many roles beyond the security team:
- Leadership provides oversight and resources
- Technology teams understand systems
- Legal teams navigate compliance requirements
- Human resources handles personnel-related incidents
- Physical security manages facility access during investigations
This broader involvement can feel chaotic initially, but organizations that invest in cross-functional preparation tend to handle incidents more smoothly.
What This Means in Practice
The updated guidance reflects a field that has learned from experience. There is no such thing as perfect incident response, but organizations can build cyber resilience through preparation, clear procedures, and realistic expectations. The goal is not to prevent every incident, but to handle incidents effectively when they inevitably do occur, and learn from each experience.
Moving Forward
For organizations reviewing their cybersecurity incident response capabilities, the updated guidance offers a useful framework for assessment. Start by evaluating your current capabilities against the CSF 2.0 functions to identify where preparation efforts might have the most impact and improve your cyber resllience.
The complete NIST SP 800-61r3 publication and additional resources are available through the NIST Cybersecurity Framework Resource Center.
